In today’s fast-paced world of software development, the need for agility and speed is paramount. DevOps had emerged as a transformative approach to encourage collaboration between development and operation teams at an unprecedented pace.
But, in the race for rapid deployment, there should be no risk in maintaining security. That is where DevSecOps: an amalgamation of development, security, and operations, entered. It’s not just a buzzword but a paradigm shift in our approach to software development.
Embark on a journey with me through this blog, where we delve into the intricacies of DevSecOps, uncovering how it surpasses traditional security measures.
What is DevSecOps?
In traditional software development, security measures are often implemented as a separate phase. This is mostly performed after the development is complete. DevSecOps seeks to break down the silos between – development, security, and operations by integrating security practices into every stage of the development process.
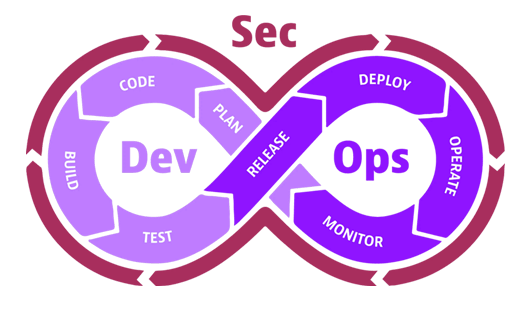
DevSecOps aims to foster teamwork and collective responsibility across the entire software development process.
You might be wondering where it all began. Well, you can get the answer in the next section.
Keep reading!
The Evolution of DevSecOps
The evolution from DevOps to DevSecOps marks a significant paradigm shift in response to the growing complexities of modern software development and the imperative need for enhanced security measures.
In the early 2010s, the advent of DevOps aimed to bridge the traditional gap between development and operations teams. To streamline the software development lifecycle (SDLC) these were the focus:
- Collaboration
- Communication
- Automation
This era witnessed the rise of Continuous Integration/Continuous Deployment (CI/CD) pipelines, enabling faster and more reliable software releases.
However, as the technological landscape evolved, it became apparent that integrating security into the development process was paramount.
This gave birth to the concept of DevSecOps by the mid-2010s. Two vital things became popular as this new concept gained prominence:
- The “shift-left” approach emerged, advocating for the early identification and mitigation of security issues.
- Automated security testing tools, such as static analysis, dynamic analysis, and interactive application security testing.
DevSecOps addressed the limitations of traditional security measures applied after development or during deployment. The goal was to embed security into the DevOps culture proactively.
By the late 2010s, organizations increasingly adopted DevSecOps to create a resilient and secure software development process.
This evolution represents a logical response to the changing technological landscape, emphasizing the importance of security in an era of continuous innovation and sophisticated cyber threats.
Did you know?
When we talk about DevSecOps, the concept of a DevSecOps pipeline comes into play. It’s a crucial step in the DevSecOps process, making your final product more secure and robust.
Let’s get to know the pipeline in detail!
The DevSecOps Pipeline
A comprehensive DevSecOps pipeline involves a series of automated and integrated processes that ensure security is embedded throughout the entire software development lifecycle.
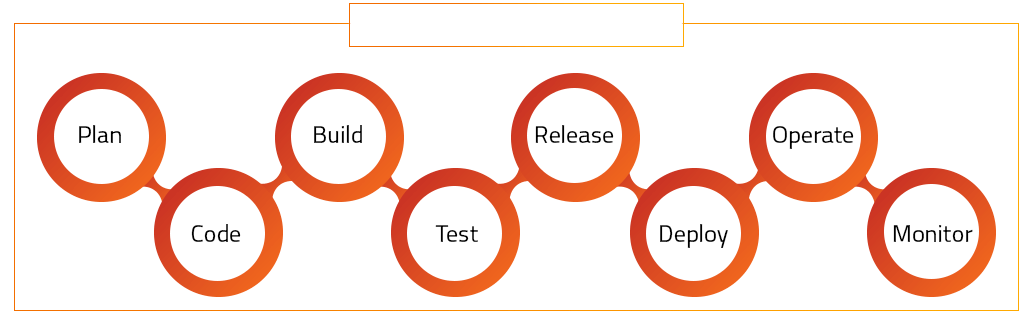
Here are the major 8 steps to building the perfect product while ensuring its security with DevSecOps:
1. PLAN
- Objective: To define security requirements and plan the development and deployment strategy.
- Activities to be performed:
-
- Risk Assessment: Conduct a comprehensive assessment to identify and evaluate potential risks.
- Security Policy Definition: Establish security policies and compliance requirements.
- Threat Modeling: Analyze and model potential security threats.
2. CODE
- Objective: To integrate security practices into the coding process.
- Activities to be performed:
-
- Static Application Security Testing (SAST): Analyze source code for security vulnerabilities.
- Code Reviews: Conduct manual reviews focusing on security best practices.
- Security Linters: Use automated tools to enforce coding standards and identify potential security issues.
3. BUILD
- Objective: To automate the build process while ensuring security.
- Activities to be performed:
-
- Dependency Scanning: Scan third-party dependencies for known vulnerabilities.
- Build Automation: Automate secure and versioned artifact creation.
- Unit Testing: Include security-focused unit tests.
4. TEST
- Objective: To conduct various security tests to identify vulnerabilities.
- Activities to be performed:
-
- Dynamic Application Security Testing (DAST): Test the running application for security vulnerabilities.
- Security-focused Integration Testing: Test interactions between components for security weaknesses.
- Penetration Testing: Simulate cyberattacks to identify potential vulnerabilities.
5. RELEASE
- Objective: To ensure that only secure artifacts are approved for release.
- Activities to be performed:
-
- Security Review: Perform a final security review before approving the release.
- Artifact Approval: Approve only secure artifacts for deployment.
6. DEPLOY
- Objective: To automate secure deployments and ensure infrastructure security.
- Activities to be performed:
-
- Infrastructure as Code (IaC) Security: Validate and scan infrastructure configurations for security compliance.
- Container Security: Scan container images for vulnerabilities.
- Automated Deployment: Automate deployment processes, integrating security measures.
7. OPERATE
- Objective: To maintain and operate the application securely.
- Activities to be performed:
-
- Access Management: Implement and enforce proper access controls.
- Security Patching: Regularly apply security patches and updates.
- Configuration Management: Ensure secure configurations are maintained.
8. MONITOR
- Objective: To continuously monitor for security threats and incidents.
- Activities to be performed:
-
- Continuous Security Monitoring: Monitor applications and infrastructure for security incidents.
- Logging and Auditing: Implement robust logging mechanisms for auditing.
- Incident Response: Develop and test incident response plans.
This pipeline is designed to integrate security throughout the entire software development lifecycle, from planning to monitoring. It emphasizes automation, continuous testing, and collaboration between development, operations, and security teams to ensure a secure and resilient application.
Quick fact: Did you know that Gen AI plays a crucial role in boosting DevSecOps? Get an additional read on how these two seamlessly complement each other.
Now that you’re all geared up with the concept of DevSecOps, let me help you understand its advantages.
Benefits of DevSecOps
DevSecOps can bring these benefits to your table, helping you fortify your software development lifecycle:
- It integrates security early to identify and address vulnerabilities, minimizing the risk of security incidents in software development.
- It embraces automation for faster and more reliable software delivery, ensuring security is seamlessly integrated into the deployment pipeline.
- It fosters collaboration among development, operations, and security teams, promoting a collective approach to addressing and sharing security considerations.
- It meets regulatory requirements by integrating security controls and documentation into development and deployment processes.
- It enables continuous monitoring for real-time insights into application and infrastructure security, facilitating quick responses to incidents and continuous improvement.
- It promotes secure coding practices by encoding security configurations and policies as code for version control, auditability, and consistent application of security measures.
- It cultivates a security-aware culture, encouraging proactive mindsets and contributing to a more resilient and secure development environment.
Next, let me guide you through the best practices of DevSecOps for optimal results.
Best Practices of DevSecOps
Here are best practices you need to follow:
- Encourage collaboration: Foster teamwork among development, security, and operations teams to integrate security seamlessly throughout the software development lifecycle.
- Incorporate security measures: At the earliest stages of development, try incorporating security measures rather than addressing them as an afterthought. This can be achieved by using automation tools and processes that help build security into the software.
- Automate security processes: To reduce manual errors and improve efficiency, try automating your security processes. This can be achieved by using technology to perform repeatable tasks with minimal human assistance.
- Track progress: Monitor the progress of DevSecOps practices at each stage of the software development lifecycle. Use metrics and analytics to assess the effectiveness of security practices and identify areas for improvement.
- Educate your developers: Raise awareness among developers about secure coding practices to ensure the creation of secure software from the outset. Provide training, resources, and tools to support developers in writing secure code.
While DevSecOps may pose some challenges, the benefits of implementing DevSecOps often outweigh the difficulties, and organizations find that the investment in a more secure and efficient development process is worthwhile in the long run.
Hence, in an era where cybersecurity threats are pervasive, DevSecOps stands as a powerful methodology that not only enhances the security posture of web applications but also contributes to a proactive and security-aware organizational culture.
Reach out to us at Nitor Infotech to fast forward your business with our cutting-edge tech services.






